Cloud Computing and Security
What is your responsibility as a customer
and what is the responsibility of your provider
Cloud computing is the delivery of computer services via the internet. This is an oversimplification, but hopefully it will be made clearer throughout the article.
It used to be that databases, software, storage and networking were all done locally, at the office/building where a business was run. There was often an in-house IT person/s or outsourced Managed IT company that would handle all the complications involved in operating all that hardware on-site. But since the COVID crisis, it has become more cost-efficient to use a third-party service to house and manage all that hardware and for customers to access it remotely.
Investment in cloud computing increased rapidly since the 2020, changing the landscape of digital technology as vendors and employees moved away from offices to work. Cloud computing revenues, said IBM, reached $219 billion in 2020, and analysts expect the industry to further grow to $791 billion by 2028.
There are several types of cloud services, but these are the 4 most basic.
Software as a Service (SaaS) – In all likelihood you already use Saas services. These are application that run directly from a browser. examples Dropbox, Google Drive, ZenDesk
Platform as a Service (PaaS) – In this case, the cloud service provides the customer with the infrastructure but gives developers access so they can build, test and customize apps. example Elastic Beanstalk, Netlify, Heroku
Infrastructure as a service (IaaS) – In this case, the company would provide all the physical infrastructure required by the company so that they don’t have to purchase/secure all the physical hardware themselves. This is obviously much more cost effective and since the cloud service is set up to offer this service, it is usually much faster and flexible. This sort of service is typically used by companies that build their own software ex. DigitalOcean, Linode, Rackspace, Amazon Web Services
Private Cloud Service – Your own storage where you control everything.
Depending on what kind of service you are procuring, your responsibility as a customer varies. Hopefully the below table can shed some light on how responsibility is distributed. It is very important to understand where the cloud provider’s duty of care ends and where the customer (yours) begins. The onus is on the customer to understand what data is at risk and how to protect it.
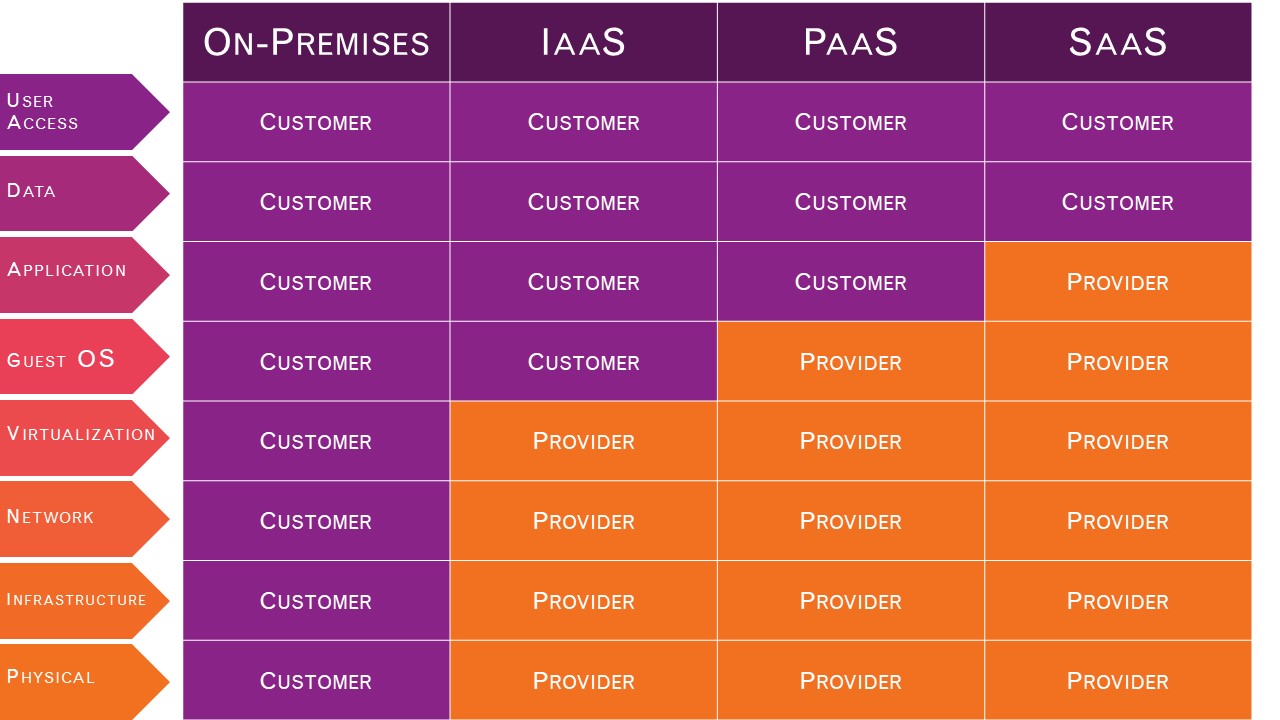
The provider must ensure that their infrastructure is secure and that their clients’ data and applications are protected, while the user must take measures to fortify their application and use strong passwords and authentication measures.
Information and Data
All of your data, images, documents, spreadsheet, databases etc. are the owner’s responsibility. Proper backup of all integral business assets is a must. In this case, before a move to the cloud, it is within the company’s best interest to conduct a security audit. Learn more about data security and if your data is vulnerable.
Devices
Customers must ensure that any devices being used by employees are secure. How they are accessing the network and how quickly they can access it is all integral to running a business smoothly. It is important that these roads are secure. Security protocols on devices, boundaries to access information, ability to remotely wipe and recover devices are all essential in securing your cloud access. In today’s environment, businesses are more device friendly. Find out more about securing your workplace devices.
Accounts and Identities
Having proper internal file architecture and limited access to sensitive areas is also something that must be clearly defined. Each user should have specified roles, access and abilities within. In addition, complex passwords and two factor authentication. If you are usure of how secure your business is, learn more about how to identify security risks.
