
LOCKY made its debut a week ago, and impacted half a million users around the globe in a day. The numbers have escalated alarmingly since then as this latest crypto-ransomware, developed by the same dark minds behind Dridex banking malware, spreads across platforms and continents.
As detailed by researchers at Naked Security for Sophos, LOCKY encrypts a wide range of file types. These include videos, images, PDFs, program source code, and Office files. As well as files in any directory on any mounted drive that the infected computer can access. This is important because this will also include removable drives plugged in at the time or network shares that are accessible like servers and other people’s computers. That is a lot of potential damage. Extend that to a case where an infected user is connected to the network using administrator access and controls; the damage could be widespread. Locky will also encrypt Bitcoin wallet files it finds, thereby stealing any bitcoin that could have paid ransom. Affected users will see this screen appear:
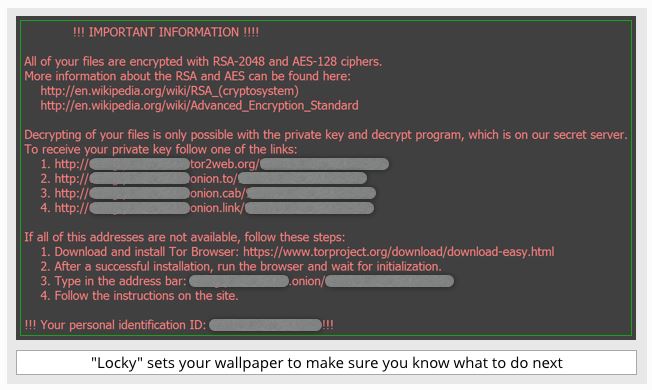
But then LOCKY takes things further by removing any Volume Snapshot Service (VSS) files or “shadow copies.” If you use Windows, you know those are the current of live backups Windows takes of work in progress – we all rely on those for when we forget to save, or the system crashes. Unfortunately, for some users these shadow copies have simply become their backup system.
We’re warning users to eware of phishing emails, in particular MS Word documents that masquerade as invoices requiring urgent payments, or bank statements. These will contain malicious macros that launch the malware. Once it gets onto a computer connected to ANY network, it will spread and contaminate rapidly. And any removable devices will also become contaminated, putting others at risk.
If you suspect you’ve been hit, time is crucial. Contact your support people immediately. We’re here for you. And shut your computer down. You need to cut yourself off from the network immediately. Expect that you will not be using your computer for some time. Expect that you will need to shutdown the network. Given that the encryption is so powerful, the only recourse victims have is to restore from an untainted backup. Or face paying the ransom with no guarantees.
Here’s what you can do to stay safer:
- make regular backups and keep one off-site
- do not enable macros in emails and attachments
- be suspicious of attachments from unknown/untrusted sources
- do not stay signed on with administrator privileges any longer than you need
- keep your security patches up to date
Thanks for reading and hope we helped!
Cheryl Biswas, Editor
